티스토리 뷰
딱히 업무에 필요는 없는데, gpg 를 이용하여 파일 암호화를 테스트 해보기로 하였다.
우선, gpg 가 설치 되어 있는지 확인 하고 설치 되어 있지 않다면 설치 하도록 한다.
root@freecatz-web:~# apt-cache search gpg | grep "GNU Privacy Guard"
gpg - GNU Privacy Guard -- minimalist public key operations
kgpg - graphical front end for GNU Privacy Guard
root@freecatz-web:~# apt install gpg
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following additional packages will be installed:
dirmngr gnupg gnupg-l10n gnupg-utils gpg-agent gpg-wks-client gpg-wks-server gpgconf gpgsm libassuan0 libksba8 libnpth0
pinentry-curses
Suggested packages:
dbus-user-session pinentry-gnome3 tor parcimonie xloadimage scdaemon pinentry-doc
The following NEW packages will be installed:
dirmngr gnupg gnupg-l10n gnupg-utils gpg gpg-agent gpg-wks-client gpg-wks-server gpgconf gpgsm libassuan0 libksba8
libnpth0 pinentry-curses
0 upgraded, 14 newly installed, 0 to remove and 23 not upgraded.
Need to get 7,089 kB of archives.
After this operation, 14.9 MB of additional disk space will be used.
Do you want to continue? [Y/n] y
... 중략 ...
Setting up gpg-wks-client (2.2.12-1+deb10u1) ...
Setting up gnupg (2.2.12-1+deb10u1) ...
Processing triggers for libc-bin (2.28-10) ...
root@freecatz-web:~# exit
logout
시스템에 gpg 가 설치 되어 있다. 일반 사용자 계정으로 전환 하여 파일 암호화를 테스트를 진행 한다.
freecatz@freecatz-web:~$ gpg --version
gpg (GnuPG) 2.2.12
libgcrypt 1.8.4
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <https://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Home: /home/freecatz/.gnupg
Supported algorithms:
Pubkey: RSA, ELG, DSA, ECDH, ECDSA, EDDSA
Cipher: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH,
CAMELLIA128, CAMELLIA192, CAMELLIA256
Hash: SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224
Compression: Uncompressed, ZIP, ZLIB, BZIP2
암호화 대상의 파일을 생성 한다.
freecatz@freecatz-web:~$ echo "gpg 암호화 테스트 입니다." >> gpg_test.txt
freecatz@freecatz-web:~$ cat gpg_test.txt
gpg 암호화 테스트 입니다.
gpg 를 이용하여 파일 암호화를 진행 한다.
freecatz@freecatz-web:~$ gpg -c gpg_test.txt
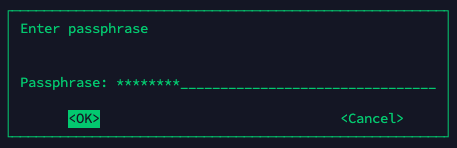

파일 암호화에 사용할 문자열을 2차례 입력 한다.
gpg: directory '/home/freecatz/.gnupg' created
gpg: keybox '/home/freecatz/.gnupg/pubring.kbx' created
gpg_test.txt 파일을 암호화한 gpg_test.txt.gpg 파일이 생성 되었다.
freecatz@freecatz-web:~$ ls -al gpg_test.*
-rw-r--r-- 1 freecatz freecatz 35 Jan 28 07:47 gpg_test.txt
-rw-r--r-- 1 freecatz freecatz 118 Jan 28 07:49 gpg_test.txt.gpg
file 명령어로 암호화된 파일임을 알 수 있다.
freecatz@freecatz-web:~$ file gpg_test.txt.gpg
gpg_test.txt.gpg: GPG symmetrically encrypted data (AES256 cipher)
암호화 이전의 원본 파일을 삭제 한다.
freecatz@freecatz-web:~$ rm -rf gpg_test.txt
암호화된 파일을 복호화 한다.
freecatz@freecatz-web:~$ gpg gpg_test.txt.gpg
gpg: WARNING: no command supplied. Trying to guess what you mean ...
gpg: AES256 encrypted data
gpg: encrypted with 1 passphrase
freecatz@freecatz-web:~$ cat gpg_test.txt
gpg 암호화 테스트 입니다.
암호화에 사용한 문자열을 입력 하지 않았는데도, 복호화가 진행 된다.
복호화된 파일과 홈디렉토리의 .gnupg 디렉토리를 를 삭제 하고 다시 테스트해 보자.
freecatz@freecatz-web:~$ rm -rf gpg_test.txt ~/.gnupg
freecatz@freecatz-web:~$ gpg gpg_test.txt.gpg
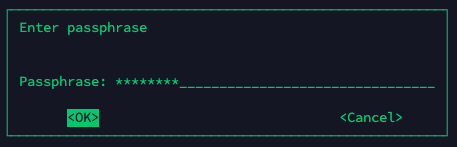
암호화에 사용하였던 문자열을 입력 한다.
freecatz@freecatz-web:~$ gpg gpg_test.txt.gpg
gpg: directory '/home/freecatz/.gnupg' created
gpg: keybox '/home/freecatz/.gnupg/pubring.kbx' created
gpg: WARNING: no command supplied. Trying to guess what you mean ...
gpg: AES256 encrypted data
gpg: encrypted with 1 passphrase
복호화된 파일의 내용을 확인해 본다.
freecatz@freecatz-web:~$ cat gpg_test.txt
gpg 암호화 테스트 입니다.
gpg 기본 암호화 알고리즘은 AES256 이며, 다른 알고리즘을 선택 하고 싶을 경우 '--cipher-algo' 옵션을 사용 한다.
freecatz@freecatz-web:~$ gpg -c --cipher-algo 3DES gpg_test.txt
현재 gpg 2.2.12 에서 지원 하는 암호화 알고리즘과 다양한 옵션에 대해서는 아래의 명령어로 확인 한다.
freecatz@freecatz-web:~$ gpg -h
gpg (GnuPG) 2.2.12
libgcrypt 1.8.4
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <https://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Home: /home/freecatz/.gnupg
Supported algorithms:
Pubkey: RSA, ELG, DSA, ECDH, ECDSA, EDDSA
Cipher: IDEA, 3DES, CAST5, BLOWFISH, AES, AES192, AES256, TWOFISH,
CAMELLIA128, CAMELLIA192, CAMELLIA256
Hash: SHA1, RIPEMD160, SHA256, SHA384, SHA512, SHA224
Compression: Uncompressed, ZIP, ZLIB, BZIP2
Syntax: gpg [options] [files]
Sign, check, encrypt or decrypt
Default operation depends on the input data
Commands:
-s, --sign make a signature
--clear-sign make a clear text signature
-b, --detach-sign make a detached signature
-e, --encrypt encrypt data
-c, --symmetric encryption only with symmetric cipher
-d, --decrypt decrypt data (default)
--verify verify a signature
-k, --list-keys list keys
--list-signatures list keys and signatures
--check-signatures list and check key signatures
--fingerprint list keys and fingerprints
-K, --list-secret-keys list secret keys
--generate-key generate a new key pair
--quick-generate-key quickly generate a new key pair
--quick-add-uid quickly add a new user-id
--quick-revoke-uid quickly revoke a user-id
--quick-set-expire quickly set a new expiration date
--full-generate-key full featured key pair generation
--generate-revocation generate a revocation certificate
--delete-keys remove keys from the public keyring
--delete-secret-keys remove keys from the secret keyring
--quick-sign-key quickly sign a key
--quick-lsign-key quickly sign a key locally
--sign-key sign a key
--lsign-key sign a key locally
--edit-key sign or edit a key
--change-passphrase change a passphrase
--export export keys
--send-keys export keys to a keyserver
--receive-keys import keys from a keyserver
--search-keys search for keys on a keyserver
--refresh-keys update all keys from a keyserver
--import import/merge keys
--card-status print the card status
--edit-card change data on a card
--change-pin change a card's PIN
--update-trustdb update the trust database
--print-md print message digests
--server run in server mode
--tofu-policy VALUE set the TOFU policy for a key
Options:
-a, --armor create ascii armored output
-r, --recipient USER-ID encrypt for USER-ID
-u, --local-user USER-ID use USER-ID to sign or decrypt
-z N set compress level to N (0 disables)
--textmode use canonical text mode
-o, --output FILE write output to FILE
-v, --verbose verbose
-n, --dry-run do not make any changes
-i, --interactive prompt before overwriting
--openpgp use strict OpenPGP behavior
(See the man page for a complete listing of all commands and options)
Examples:
-se -r Bob [file] sign and encrypt for user Bob
--clear-sign [file] make a clear text signature
--detach-sign [file] make a detached signature
--list-keys [names] show keys
--fingerprint [names] show fingerprints
Please report bugs to <https://bugs.gnupg.org>.
- Total
- Today
- Yesterday
- ssh
- Review
- devel
- SSL
- Flutter
- Fun
- dart
- web
- HTTP
- Linux
- kotlin
- springboot
- MySQL
- food
- Android
- Java
- samba
- json parse
- devtools
- 엘리스센터
- Security
- Mobile
- 맛집
- TIP
- place
- JavaScript
- Compile
- Spring
- gpkiapi
- development
| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 |
